Global CyberSecurity
Credit Card Skimmer Hidden in Fake Facebook Pixel Tracker
Post Views: 1,088 In recent months, we have encountered a number of cases where attackers inject malware into website software that allows for ...
Global CyberSecurity
Web Shells: Types, Mitigation & Removal
Post Views: 1,649 Web shells are malicious scripts that give attackers persistent access to compromised web servers, enabling them to execute commands and ...
Global CyberSecurity
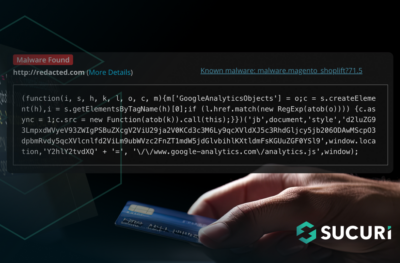
Magento Shoplift: Ecommerce Malware Targets Both WordPress & Magento CMS
Post Views: 1,598 We often write about malware that steals payment information from sites built with Magento and other types of e-commerce CMS. ...
Global CyberSecurity
WordPress Vulnerability & Patch Roundup March 2024
Post Views: 901 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are ...
Global CyberSecurity
Sign1 Malware: Analysis, Campaign History & Indicators of Compromise
Post Views: 911 A new client recently came to us reporting seemingly random pop ups occurring on their website. While it was clear ...
Global CyberSecurity
What is .htaccess Malware? (Detection, Symptoms & Prevention)
Post Views: 857 The .htaccess file is notorious for being targeted by attackers. Whether it’s using the file to hide malware, redirect search ...
Global CyberSecurity
Sucuri WordPress Plugin Updates for 2024
Post Views: 958 At Sucuri, we believe in making the internet safe for everyone. One way we show this is through our free ...