Published on 10/26/2020 – Last Updated on 10/26/2020 by OTC
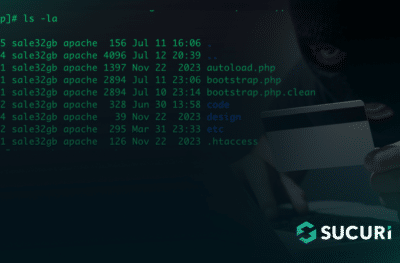
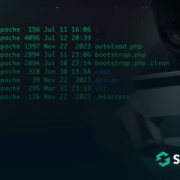
A PHP shell containing multiple functions can easily consist of thousands of lines of code, so it’s no surprise that attackers often reuse the code from some of the most popular PHP web shells, like WSO or b374k.
After all, if these popular (and readily available) PHP web shells do the job, there’s no need to code an entirely new tool. Instead of completely writing a new PHP shell, attackers are simply masking or cloaking the pre-existing code by using a variety of different obfuscation techniques to avoid detection.
Continue reading P.A.S. Fork v. 1.0 — A Web Shell Revival at Sucuri Blog.










Comments