Global CyberSecurity
Vulnerability & Patch Roundup — January 2025
Post Views: 908 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are ...
Global CyberSecurity
Sucuri WAF Now Supports HTTP/3: A Faster and More Secure Web Experience
Post Views: 535 We’re excited to announce that the Sucuri Web Application Firewall (WAF) now supports HTTP/3, the latest version of the HTTP ...
Global CyberSecurity
Malware Redirects WordPress Traffic to Harmful Sites
Post Views: 652 Recently, a customer approached us after noticing their website was redirecting visitors to a suspicious URL. They suspected their site ...
Global CyberSecurity
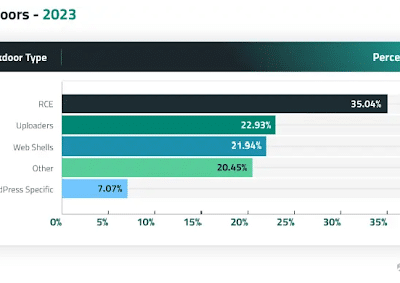
Backdoors: The Hidden Threat Lurking in Your Website
Post Views: 925 Website backdoors are a silent yet deadly threat to website security. These stealthy mechanisms bypass standard authentication, providing attackers with ...
Global CyberSecurity
Japanese Spam on a Cleaned WordPress Site: The Hidden Sitemap Problem
Post Views: 1,037 While investigating a compromised WordPress site, we discovered a malware infection causing Japanese spam links to appear in Google search ...
Global CyberSecurity
Stealthy Credit Card Skimmer Targets WordPress Checkout Pages via Database Injection
Post Views: 579 Recently, we released an article where a credit card skimmer was targeting checkout pages on a Magento site. Now we’ve ...
Global CyberSecurity
Vulnerability & Patch Roundup — December 2024
Post Views: 966 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are ...