Published on 03/10/2021 – Last Updated on 03/10/2021 by OTC
Bad actors often leverage creative techniques to conceal malicious behaviour and harvest sensitive information from ecommerce websites.
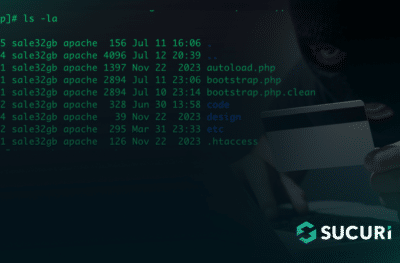
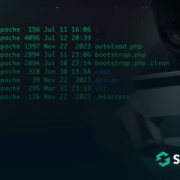
A recent investigation for a compromised Magento 2 website revealed a malicious injection that was capturing POST request data from site visitors. Located on the checkout page, it was found to encode captured data before saving it to a .JPG file.
Malicious Injection Behavior
The following PHP code was found injected to the file ./vendor/magento/module-customer/Model/Session.php.
Continue reading Magento 2 PHP Credit Card Skimmer Saves to JPG at Sucuri Blog.










Comments