Published on 07/28/2021 – Last Updated on 07/28/2021 by OTC
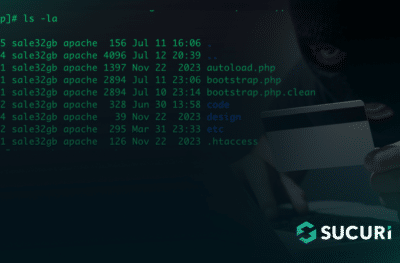
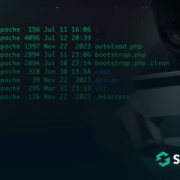
Recently one of our analysts, Weston H., found a very interesting credit card stealer in a Magento environment which loads a malicious JavaScript without using any script tags. In this post I will go over how it was found, how to decode it and how it works!
One of our clients was reporting that one of their website visitors was receiving a warning from their antivirus program when navigating to their checkout page:
Calls were being made to a known malicious domain that was already blacklisted by multiple vendors for distributing malware and involvement in carding attacks:
This certainly indicated that a card stealer was present somewhere on our client’s website.
Continue reading Stylish Magento Card Stealer loads Without Script Tags at Sucuri Blog.










Comments